Wallet Overview
When it comes to securing your cryptocurrencies it is important to understand the underlying functionally of blockchain. Simply put we have a private key that allows us the ability to interact with a public address on the blockchain where the cryptocurrency and tokens reside.
There are 3 main ways of interacting with cryptocurrencies which include Cold Wallets, Hot Wallets and Exchanges (ie. Coinbase, Gemini, Bianance) where seemingly complex we will help to demystify.
Cold Wallets – Hardware Wallets
These wallets in particular the Nano Ledger and Trezor store the private key on a USB device that is only used to sign transactions on the blockchain.
PERKS: The private keys have never seen the internet meaning in short that nobody else has access to sign (move, trade) crypto without it.
This level of security should be used for storing your crypto long term as the process of signing multiple transactions on the blockchain with each device can become cumbersome. Your own personal crypto vault where you hold the keys to your crypto.
Hot Wallets – Software Apps
These wallets consists of the likes of Coinbase Wallet, Exodus wallet, Trust Wallet, Metamask and other software wallets where your private key has the ability to be exposed to the internet.
Why is that a bad thing?
Well anyone with your private key can sign transactions in your name and (sent, trade) your crypto from your blockchain account.
Exchanges – Centralized Cryptocurreny Exchanges
The like of Coinbase is a platform where you can buy and sell crypto but the key takeaway is that Coinbase is considered to many as custodial. They hold all the private keys to your crypto and signs the transactions on your behalf when you send and trade.
The downfall of this process is that if the exchange is ever successfully hacked an attacker can not only get ahold of your private keys but everyone else and thus move and sell everything.
Now the like of an organization such as Coinbase has taken multiple layers of security to protect against this attack but if you held your private keys on a hardware device you would not have to worry about this.
Hardware Wallets
Two of the industry leading hardware wallets are Nano Ledger and Trezor and provide secure private key security.
Ledger Nano
Lauded as one of the first crypto hardware wallets and has two different products:
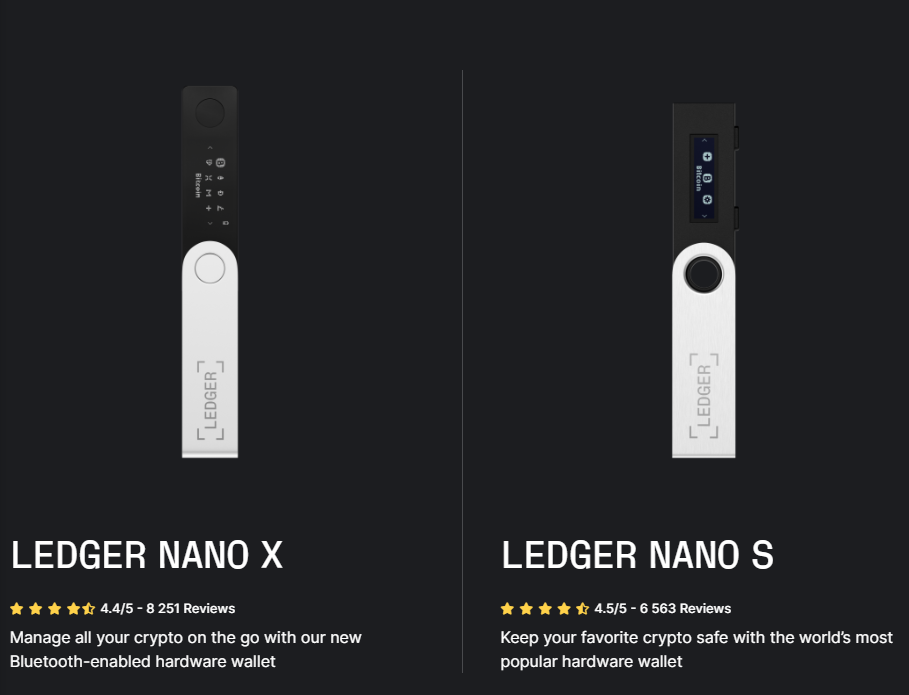
Comparison Breakdown
| Ledger Nano X | Ledger Nano S | |
| Wallet Type | Hardware | Hardware |
| Connection | USB & Bluetooth | USB |
| Crypto Apps* | Up to 20 apps | up to 3 apps |
| Secure Chip | Yes | Yes |
| Battery | Yes | No |
| Verdict | Best for larger crypto holdings | Best smaller crypto holdings |
| Price | $149.00 US | $59.00 US |
|---|
*Apps refer to the number of coin / tokens keys that can be generated on the hardware device due to storage limitations.
Hardware Security

Consisting of a USB hardware wallet with simple 2 buttons for movement on a small digital screen the software sits on top of a custom operating systems and a certified secure chip and dual-core MCUs.
*The Ledger Nano X supports wireless low energy Bluetooth support which has custom architecture that is designed to never expose secret keys or seeds phrases.
Ledger Live
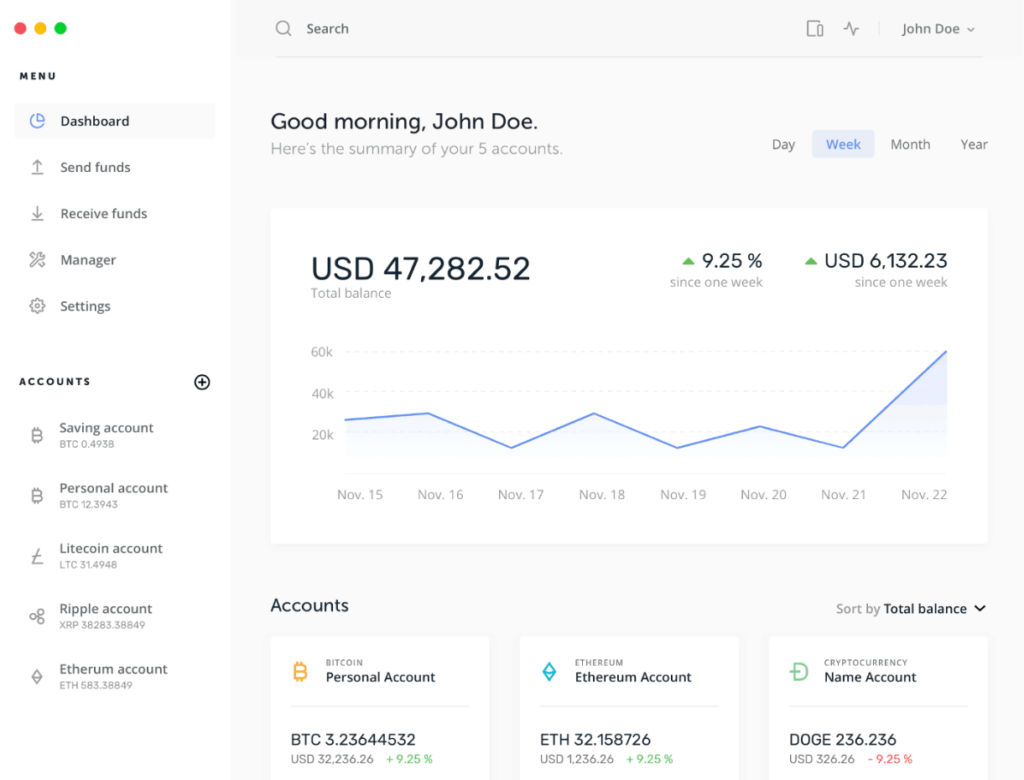
Software used to interact with your hardware wallet which can be either iOS & Android or via PC. The software contains the app store where crypto tokens private key generators can be downloaded along with the ability to buy and sell.
The software acts as the gateway for signing and interacting with the blockchain and your crypto and every action will need to be confirmed physically from the hardware device.
Trezor
The first and oldest to market small sleek cryptocurrency hardware wallet with two versions the Trezor One and the flagship Trezor Model T.

Trezor prides itself by the security measures taken not only within the device but how the device is sent to the customer. The use of secure packaging and holographic labels to indicate tampering from the supply side.
Internally, there are firmware verifications that take place along with protected key operations all within a protected bootloader. The device supports passphrases for another layer of security which helps aid against local hardware attacks.
The Trezor Model T version uses a color touch screen that makes interacting with the device easier.
Comparison Breakdown
| Trezor Model T | Trezor One | |
| Wallet Type | Hardware | Hardware |
| Connection | USB | USB |
| Crypto | 1,000+ | 1,000+ |
| Secure Chip | Yes | Yes |
| Battery | No | No |
| Verdict | Touch screen & large number of crypto holdings | Non touch screen with large number of crypto holdings |
| Price | $215.00 US | $70.00 US |
|---|
Trezorsuite
Both versions of Trezor utilize a software called the Trezorsuite which is used to add and send crypto using your private keys stored on the hardware wallets.
The Trezor has a larger integration of around 48 services and compatibility with with exchanges to include Metamask and MyEtherWallet.
The Trezorsuite software is open-source and is available on Windows, MacOS, Androd, iOS and Web Browser.
Comparison
When looking at hardware wallets both the Ledger Nano and the Trezor both offer an entry level hardware wallet and a more robust feature rich device.
Best Overall
Ledger Nano X
- Contains a battery for offline use & Bluetooth
- Large crypto compatibility and integration
- Pricing
- Secure Hardware
Overall we believe that the Ledger Nano X is the best well rounded purchase for a hardware wallet to secure your private keys.
Need Setup Help?
Here at Crypto Technical Consultants we can help set up your device live and one and one. We can help take the worry out of setting up and any issues and questions you could have along the way.
We will never ask you for any of your wallet information – EVER.
Have an issue connecting your wallet to software or just simply want to make sure you are performing all the steps correctly and that is where we step in. Cryptocurrencies and wallets can be complex but we want to make sure you understand everything along the way from beginners to advanced users.
Simply head over to our page and set up an appointment with our consultants at https://cryptotechnicalconsultants.com.